When you’re checking e-mail online in the webmail interface, it’s vital that you make sure visitors can access it with ease. So encountering error messages and connection issues – such as Chrome error warnings – can be quite frustrating.
In this post, we’ll discuss the ERR_SSL_OBSOLETE_VERSION warning in Chrome, explain why it occurs, and talk about what you can do to resolve it.
Let’s get started!
How to Fix ERR_SSL_OBSOLETE_VERSION Warning Notifications in Chrome
Starting with Google Chrome 72, one key thing has changed: the popular browser started deprecating support for legacy TLS versions. This shouldn’t come as news as, in 2019, Google and a variety of other major browsers had already revealed that they would be deprecating support for TLS 1.0 and TLS 1.1.
This is being done in order to enhance the security and performance of the browsers, and protect users from unsecured sites.
TLS is short for “Transport Layer Security”. It’s an encryption security protocol responsible for safeguarding data that is being transmitted online. In other words, it protects the information being sent between your website’s server and the end user’s browser.
At this point, TLS 1.0 and TLS 1.1 are old standards that have various limitations and fail to support many modern internet technologies. Therefore, the focus is now turning towards the newer TLS 1.2 and 1.3 versions.
These offer better security and faster speeds and are already standard for nearly all browser-based connections.
The Dangers of Using Older TLS Versions on Your Website
So what does this mean for the future of Chrome browsers, and more specifically for your website’s users? Beginning with Chrome 79, if a site is using TLS 1.0 or TLS 1.1, Chrome will display a warning notification indicating a “not secure” connection.
When the visitor clicks through for more information, they’ll see a message similar to this one:
“Your connection is not fully secure. This site uses an outdated security configuration, which may expose your information.”
Naturally, this message is likely to turn many potential visitors away.
This is similar to other types of Chrome warnings you may have seen in the past. However, it’s important to note that this particular notification is only going to grow more severe as new versions of Chrome are released.
For example, with Chrome 81 set to launch in March 2021, connections to sites using outdated security protocols will be blocked altogether.
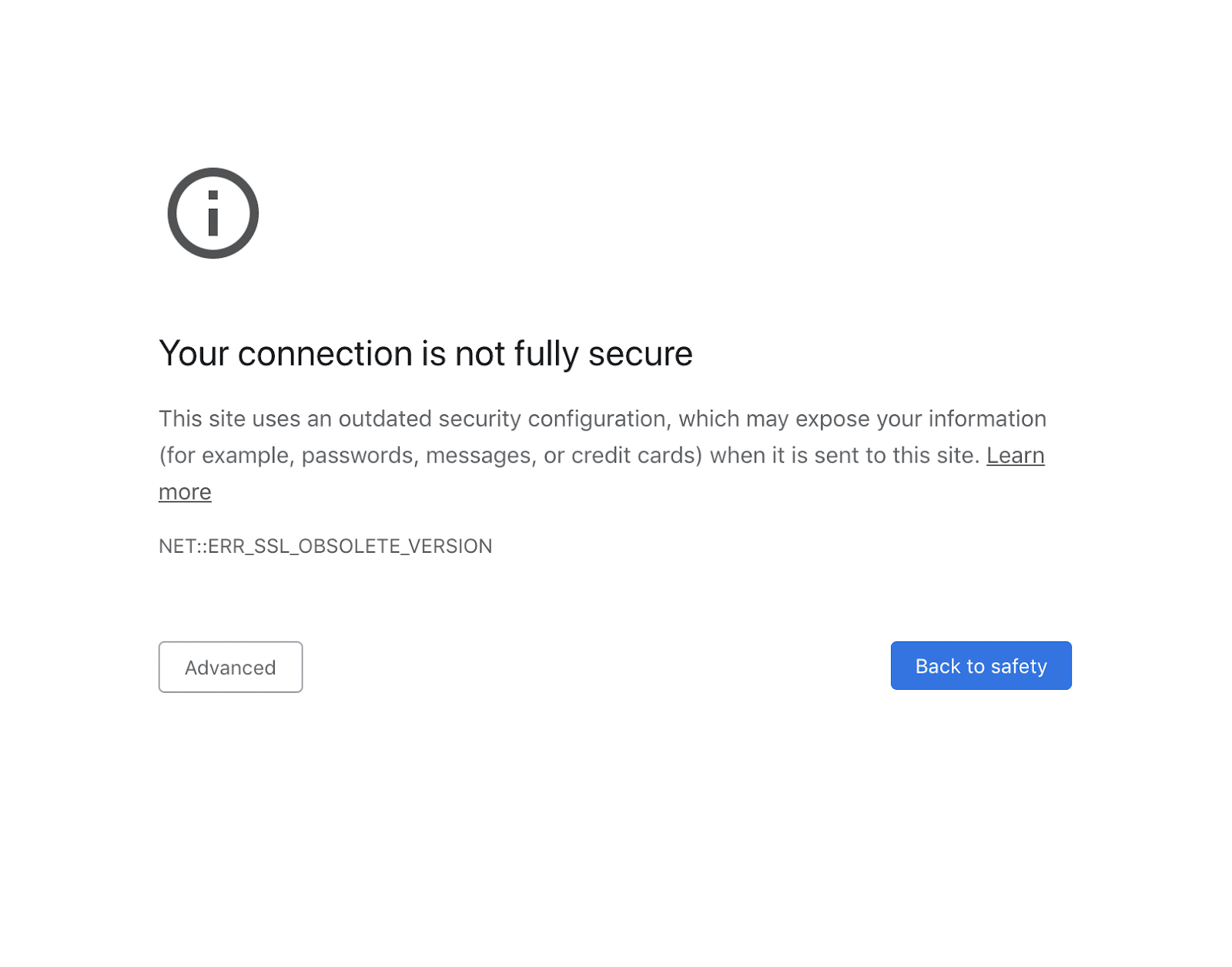
The new Chrome warning will be a full-page notification explaining that the page the browser is trying to visit is not fully secure. What’s more, it will include an ERR_SSL_OBSOLETE_VERSION message. The “obsolete version” that the warning is referring to will be either TLS 1.0 or TLS 1.1.
This is why Google is encouraging site administrators to enable TLS 1.2 or later immediately. The process for doing this will vary depending on your hosting provider, which we’ll look at shortly.
First, however, let’s talk about how to determine if this potential issue is relevant to your site.
How to Find Out What Version of TLS Your Site Is Running
If you’ve already encountered the ERR_SSL_OBSOLETE_VERSION warning, then you know that your site is only using obsolete versions of TLS. For example, you may run across this error when using Google Search Console.
However, what if you’re not sure what version of TLS is enabled on your website?
Fortunately, there are multiple potential ways to find this information. One of the simplest is to use Chrome DevTools.
You can access these tools using Command+Option+C (on a Mac) or Control+Shift+C (on Windows and Linux). Then, click on the Security tab:
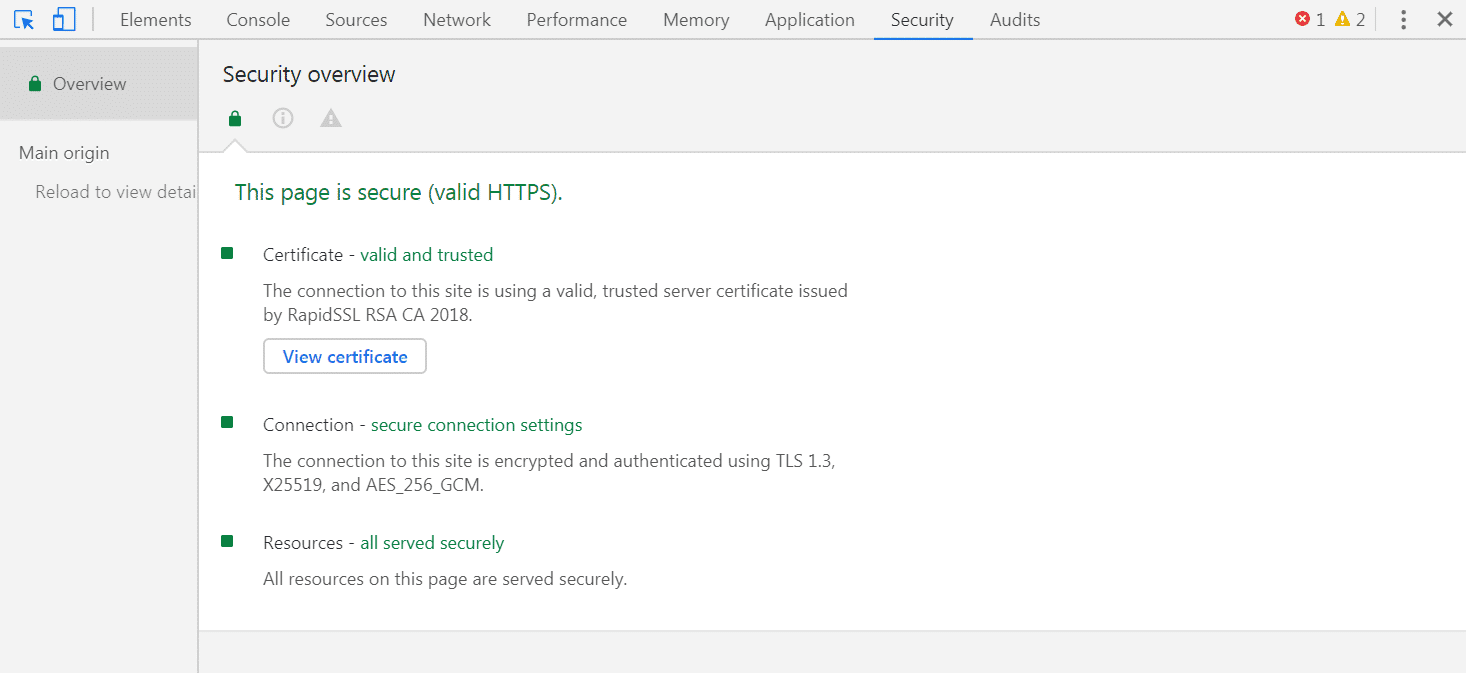
In the Security Overview, the Connection section should state what version of TLS your site is running. If that version is 1.2 or 1.3, as in the example above, you don’t need to worry about the ERR_SSL_OBSOLETE_VERSION Chrome warning. If the version is 1.0 or 1.1, then you have some work to do.
How to Enable Chrome TLS 1.2 or Later Versions
To prevent the ERR_SSL_OBSOLETE_VERSION notification, webmasters will need to enable TLS 1.2 or later on their websites.
You don’t need to deactivate support for versions 1.0 and 1.1. Instead, you just need to make sure your site enables connections via Chrome TLS 1.2 and/or 1.3, so users with newer browser versions can visit your site safely.
Struggling with downtime and WordPress issues? Kinsta is the hosting solution designed with performance and security in mind! Check out our plans
Exactly how you do this will vary significantly, based on your website’s host and setup.
The first thing you’ll need to do is verify that your hosting server supports TLS 1.2 (at the least). To do that, you can visit Qualys’ SSL Server Test, and enter in your website’s hostname:
The Qualys SSL Server Test tool
In the results, look under Configuration > Protocols for “TLS 1.2” and “TLS 1.3”: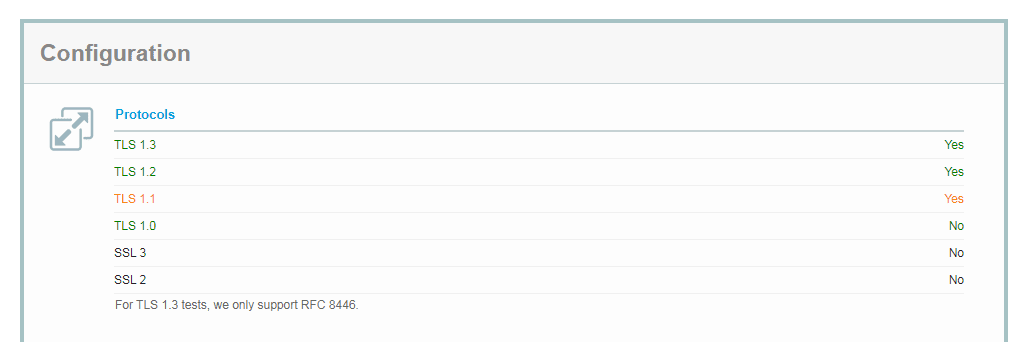
The Protocols section, outlining what versions of TLS are supported
If one or both read “Yes”, then you know that your site is configured to use TLS 1.2 or higher. At that point, you’ll want to consult your hosting provider’s documentation or contact them directly to find out how you can enable the protocol on your site.
On the other hand, if “TLS 1.2” is labeled as “No”, then it likely won’t be possible to enable that protocol and prevent the ERR_SSL_OBSOLETE_VERSION notification. In that scenario, you’ll want to communicate with your web host to find out if you can upgrade to a different plan on a server that is configured for the newer TLS protocols.
Alternatively, you could also look for a new hosting provider that will make resolving this issue simple.
Summary
Google is deprecating support for TLS 1.0 and 1.1 and that’s a big deal since Chrome is the most-used browser on the web. Therefore, if your website can’t transmit information using the newer TLS protocols, your visitors may face the ERR_SSL_OBSOLETE_VERSION Chrome warning.
The best way to avoid that notification and keep your visitors safe is to enable support for TLS 1.2 or higher. You can use Chrome DevTools and Qualys’ SSL Server Test to check and see whether your site and server enable these protocols
